iSCSI (Internet Small Computer System Interface)
iSCSI is a transport layer protocol that describes how Small Computer System Interface (SCSI) packets should be transported over a TCP/IP network.
iSCSI (Internet Small Computer System
iSCSI, which stands for Internet Small Computer System Interface, works on top of the Transport Control Protocol (TCP) and allows the SCSI command to be sent end-to-end over local-area networks (LANs), wide-area networks (WANs) or the Internet. IBMdeveloped iSCSI as a proof of concept in 1998, and presented the first draft of the iSCSI standard to the Internet Engineering Task Force (IETF) in 2000. The protocol was ratified in 2003.
How ISCSI works
iSCSI works by transporting block-level data between an iSCSI initiator on a server and an iSCSI target on a storage device. The iSCSI protocol encapsulates SCSI commands and assembles the data in packets for the TCP/IP layer. Packets are sent over the network using a point-to-point connection. Upon arrival, the iSCSI protocol disassembles the packets, separating the SCSI commands so the operating system (OS) will see the storage as a local SCSI device that can be formatted as usual. Today, some of iSCSI’s popularity in small to midsize businesses (SMBs) has to do with the way server virtualization makes use of storage pools. In a virtualized environment, the storage pool is accessible to all the hosts within the cluster and the cluster nodes nodes communicate with the storage pool over the network through the use of the iSCSI protocol.

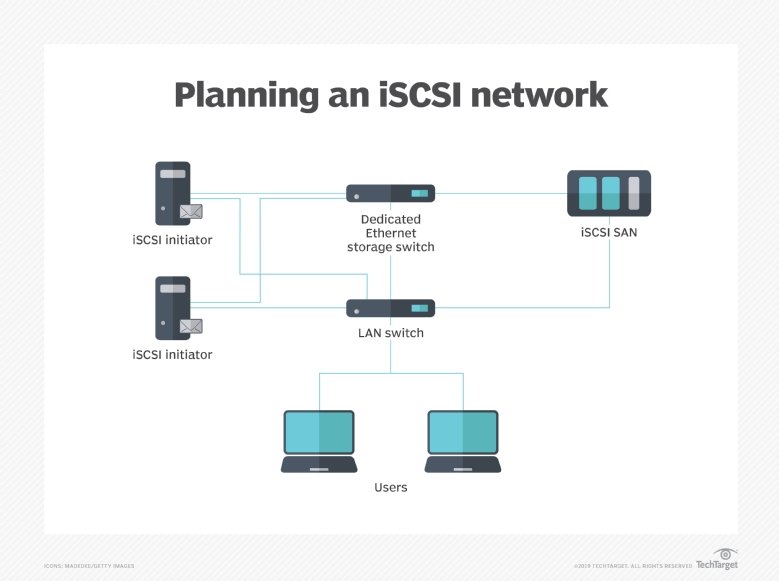
An iSCSI initiator is a piece of software or hardware that is installed in a server to send data to and from an iSCSI-based storage array or iSCSI target. The following video discusses the impact of the Microsoft Windows Server 2012 iSCSI Target software functionality, and shows how to install the iSCSI target, create an iSCSI virtual disk and use iSCSI for failover clustering.
iSCSI benefits
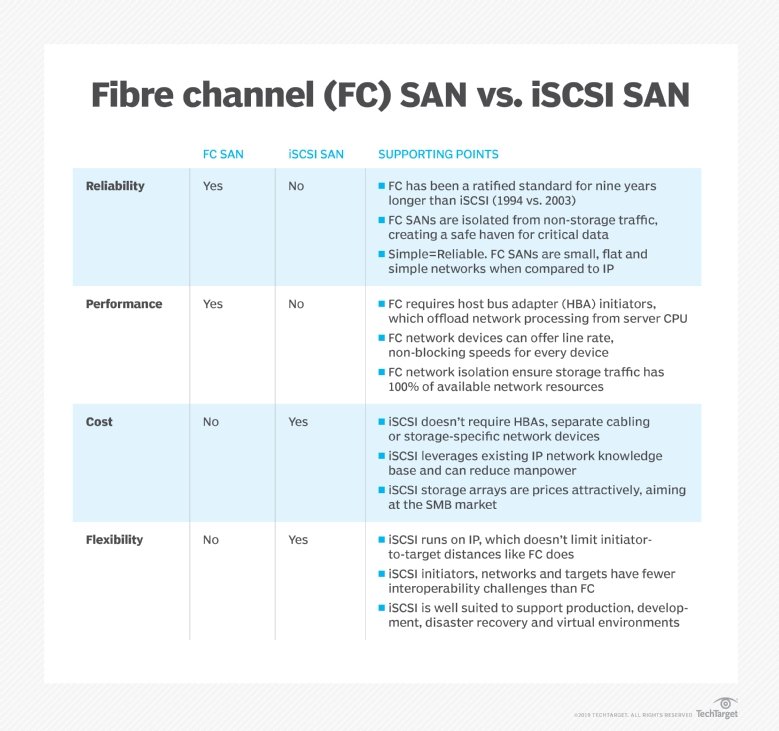
Because it uses standard Ethernet, iSCSI does not require expensive and sometimes complex switches and cards that are needed to run Fibre Channel (FC) networks. That makes it cheaper to adopt and easier to manage.
iSCSI market success
Because of concerns about performance and compatibility with other storage networks, iSCSI SANs took several years to catch on as mainstream alternatives to Fibre Channel. Start-up vendors EqualLogic Corp. and LeftHand Networks Inc. finally achieved enough success with their iSCSI storage arrays that larger vendors acquired them. In 2008, Dell Inc. bought EqualLogic for $1.4 billion and Hewlett-Packard Co. paid $360 million for LeftHand.
Fibre Channel remains a more popular storage protocol than iSCSI, but all major storage vendors now have iSCSI SAN arrays, including storage platforms that support FC and iSCSI. Systems that run FC and iSCSI are known as unified or multiprotocol storage, and they often run network-attached systems for files.
Ethernet alternatives to iSCSI
iSCSI is the most popular approach to storage data transmission over Internet Protocol (IP) networks, but there are alternatives, such as the following:
- Fibre Channel over IP (FCIP), also known as Fibre Channel tunneling, moves data between SANs over IP networks to facilitate data sharing over a geographically distributed enterprise.
- Internet Fibre Channel Protocol (iFCP) is an alternative to FCIP that merges SCSI and FC networks into the Internet.
- Fibre Channel over Ethernet (FCoE) became an official standard in 2009. Pushed by Cisco Systems Inc. and other networking vendors, it was developed to make Ethernet more suitable for transporting data packets to reduce the need for Fibre Channel. But while it is used in top-of-rack switches with Cisco servers, FCoE is rarely used in SAN switching.
- ATA over Ethernet (AoE) is another Ethernet SAN protocol that has been sold commercially, mainly by Coraid Inc. AoE translates the Advanced Technology Attachment (ATA) storage protocol directly to Ethernet networking rather than building on a high-level protocol, as iSCSI does with TCP/IP.
iSCSI security
The primary security risk to iSCSI SANs is that an attacker can sniff transmitted storage data. Storage administrators can take steps to lock down their iSCSI SAN, such as using access control lists (ACLs) to limit user privileges to particular information in the SAN. Challenge-Handshake Authentication Protocol (CHAP) and other authenticationprotocols secure management interfaces and encryption for data in motion and data at rest.